Nowadays the problem of network security is a key issue. More and more often we use Internet and mobile solutions and their customization usually associated with logging, which requires a password. Today, a few words about how to create a strong password that is secure.
Without any admission are a few key principles for creating a strong password:
a/ password length – the more characters more difficult to crack password – the minimum is 6 characters
b/ a variety of characters – make sure you use a password of at least the following types of characters:
- lower case letters (without Polish characters)
- large letters (without Polish characters)
- digits
- special characters or -+*=_!@#$%^&(){}[]|:;,.<>?/\”`~
So much for the design and content of the password. The following aspects related to security come down more to psychological issues.
a/ Definitely avoid using words associated with your real life – twarriors name, child’s name, year of birth, place of residence, etc. – based on this type of expression, you run the discovery of passwords by people in your environment and there have been incidents 😉
b/ I know it’s terribly difficult but do not use a single password in every possible place –
websites and applications on the phone – use 2-3 different variants of the same password – that’s something – very simple suggestion is to build alternans password eg .:
12ABpassword34 interchangeably with 34ABpassword12 or 34abPASSWORD12
The above example shows how easy it is to modify the same strong password to remember and use one of its variants.
c/ Periodically change your password. There is nothing worse than the same password used for a long period of time and is in addition to one of several services. Remember to change your password every six months or maybe once every quarter. I think it’s worth it.
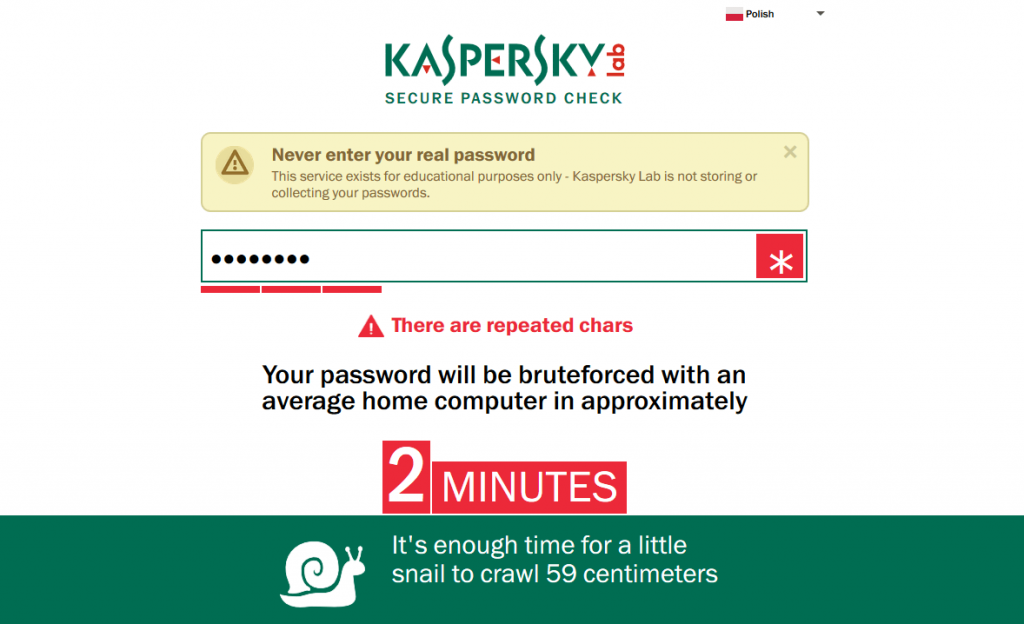
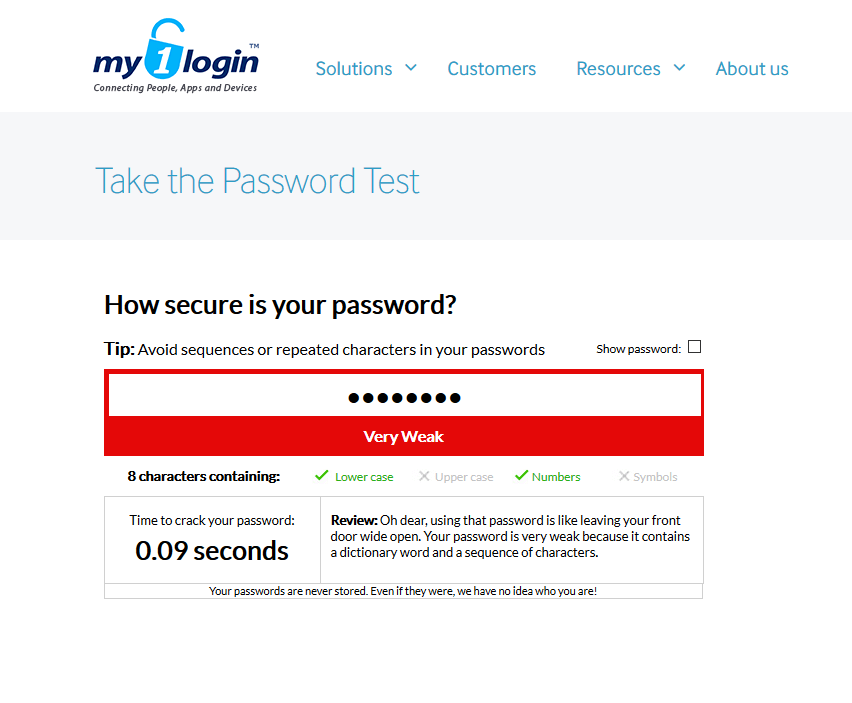
As a form of trivia I’ve included links to two pages, in which you check the strength of your current password. I think this is a nice test the more that the two websites listed below authors application graphically indicate how much time is needed to crack your password. May the days were not a second 😉